Todays Task -
- Solve 1 box on HTB
HackTheBox
Introduction
Windows is the most predominant operating system in today's world because of its easy-to-use GUI accessibility. About 85% of the market share has become a critical OS to attack. Furthermore, most organizations use Active Directory to set up their Windows domain networks. Microsoft employs NTLM (New Technology LAN Manager) and Kerberos for authentication services. Despite known vulnerabilities,
NTLM remains widely deployed, even on new systems, to maintain compatibility with legacy clients and servers.
This lab focuses on how a file inclusion vulnerability on a webpage being served on a Windows machine can be exploited to collect the NetNTLMv2 challenge of the user that is running the web server. We will use a utility called Responder to capture a NetNTLMv2 hash and later use a utility known as John the Ripper to test millions of potential passwords to see if they match the one used to create the hash. We will also be taking a deeper look at the working process of NTLM authentication and how the Responder utility captures the challenge.
Enumeration
We will begin by scanning the host for any open ports and running services with a Nmap scan. We will be using the following flags for the scan:
-p- : This flag scans for all TCP ports ranging from 0-65535
-sV : Attempts to determine the version of the service running on a port
--min-rate : This is used to specify the minimum number of packets Nmap should send per second; it speeds up the scan as the number goes higher
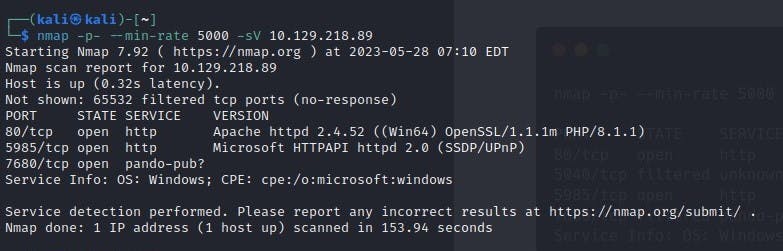
According to the results of the Nmap scan, the machine is using Windows as its operating system. Two ports were detected as open, with the Apache web server running on port 80 and WinRM on port 5985.